Are you prepared to deal with a cyberattack against your business? Would you recover after a ransomware attack, a data leak, an insider threat, or a virus? Most business owners think it can’t happen to them, but small businesses are primary targets for hackers. Unfortunately, 60% of companies go out of business after an attack, largely due to the fact that they weren’t prepared.
You don’t have to become one of these statistics if you take the time to secure your network against threats. If the concept of cybersecurity is new to you, or you don’t know what’s involved, here’s where you can start.
1. Get a cybersecurity assessment
The first and most important aspect of cybersecurity involves getting an assessment. If you don’t know where you stand, you won’t be able to protect your network. You need to know exactly what your vulnerabilities are in order to resolve them. That’s what an IT vulnerability assessment will do for you.
According to Reverus.com, a cybersecurity audit consists of the following steps:
- Equipment is installed to scan your company’s network
- An audit is performed on internal and external security postures
- Vulnerabilities are identified
- A detailed assessment report is created listing all vulnerabilities
- A consultation ensues to go over the report
- The equipment is removed and all data collected is deleted
- Your results are compared to applicable data regulations to identify compliance issues
Once these steps are completed, you can engage vulnerability management services to make improvements to secure your network. This leads to the next point…
2. Get vulnerability management services

Source: cyberchasse.com
When you’re a business owner, your time is valuable. You don’t have time to babysit your network and neither does your IT team (if you have one). Vulnerability management services will help you keep your network secure by providing continuous monitoring, evaluation, and reporting, along with fixing any vulnerabilities discovered.
These services will help you get into compliance if you are not currently aligned with data regulations. This will happen continuously so you never have to worry about getting out of compliance or allowing an unknown vulnerability to exist for too long.
Unfortunately, many vulnerabilities go long periods of time without being detected. The longest so far is 21 years. According to data sourced by Comparitech, 75% of cyberattacks in 2020 were the result of vulnerabilities that were at least two years old. If you don’t have IT pros managing your vulnerabilities, your company is at risk.
3. Educate and train your staff
Unfortunately, a large number of cyberattacks occur when employees make careless mistakes. It can happen to any business at any time. The best way to prevent this issue is through education and training.
The goal is to train your employees to adopt specific habits that protect your company’s network. For example, if you have remote employees, require them to connect to the company network through a VPN so that all traffic will be encrypted. If they happen to log on from a public Wi-Fi spot, like Starbucks, nobody can steal their login credentials.
Since this can’t be forced, the only thing you can do is train your team members into the habit. Other things, however, can be forced, like multi-factor authentication (MFA). This will be addressed in the next point.
4. Require multi-factor authentication (MFA)

Source: loginradius.com
Sometimes, cyber criminals steal login credentials, but with MFA, you have a backup plan that ensures they can’t actually log into your network. With MFA, each user is required to retrieve a code or use their fingerprint in addition to entering a username and password before the system will let them log in successfully.
MFA is one of the best security tools you can implement in your business. Even if someone falls for a phishing scheme and gives out their login credentials, you don’t have to worry about the attacker gaining access to your network.
5. Require that only registered devices may access the network
In addition to MFA, it’s a good idea to restrict access to your network by device. With this in place, each employee and contractor’s device will be known to the network and they can only log in when using that device. If they need to use a different device, they’ll have to get permission from you first.
If you want to restrict access even further, you can limit access to registered devices on known IPs. For instance, you can require that someone be in the office using your company’s internet connection in order to access the network. This will not only protect your network, but it will discourage working off the clock. For people who need access outside of the office, you can set further controls to allow just those people access from another IP address.
6. Encrypt your data end-to-end
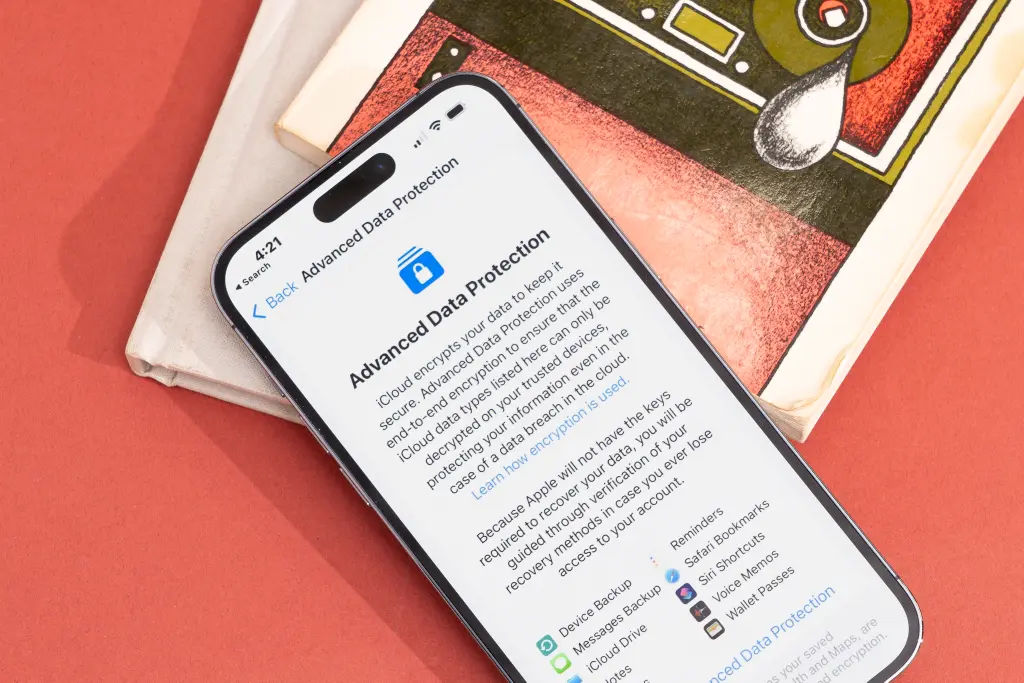
Source: nytimes.com
The ultimate in data protection is end-to-end encryption. You can’t prevent every data breach, but encryption can prevent hackers from using the data they’ve stolen, which means you don’t need to worry about getting fined thousands of dollars for violating a regulation.
Encrypted data looks like gibberish and can only be decrypted with a special key. Of course, encryption and decryption happen automatically with software, but the keys are stored separately. Even if someone does steal your data, they won’t have access to the decryption key (if you’ve set it up correctly).
If you do fall victim to a data breach, encryption is an excellent defense against the fines that a governing body may want to impose. It’s always best to use encryption because you can’t predict if or when your business will be attacked.
Network security is essential
If you haven’t already, it’s time to prioritize network security to prevent data breaches, data leaks, ransomware attacks, and other data security incidents. You can’t afford to put it off, as the cost of ignoring security can put you out of business.
Start securing your network today and if you don’t know how to begin, hire a team of IT security professionals.



