In an era of increasing digital dependence, the security of online assets has become paramount. The recent CrowdStrike outage in July 2024 serves as a stark reminder of the vulnerabilities inherent in even the most sophisticated cybersecurity infrastructures. This incident has reignited discussions around the necessity of diversifying digital and cybersecurity infrastructure to mitigate risks and ensure resilience against unforeseen disruptions.
The CrowdStrike Outage: A Case Study in Infrastructure Vulnerability
Source: strategyofsecurity.com
CrowdStrike, a leader in endpoint protection and cybersecurity, experienced a significant outage in July 2024 due to a configuration update that led to system crashes across multiple platforms. The outage was traced to a logic error in the update to the Falcon sensor, specifically targeting a newly identified threat. This error triggered crashes on systems running certain versions of Windows, leading to widespread service disruptions for businesses relying on CrowdStrike’s protection.
The outage, which CrowdStrike quickly addressed, highlights a critical flaw in cybersecurity strategies that rely too heavily on a single provider or system. Despite CrowdStrike’s best efforts, the disruption opened doors for potential threat actors, who could exploit the brief window of vulnerability. This incident underscores the importance of having a diversified approach to digital security to reduce the impact of such failures.
The Risks of Homogeneous Cybersecurity Infrastructure

Source: toptal.com
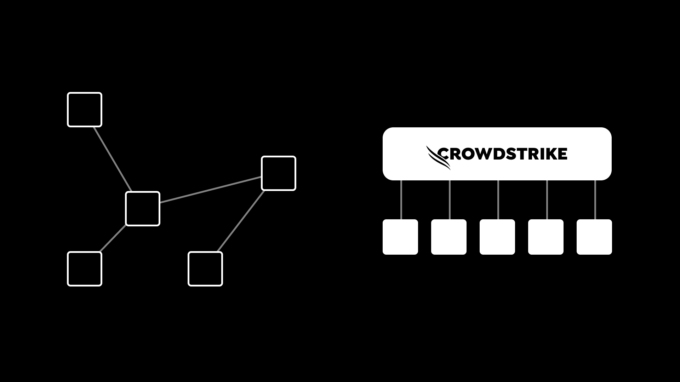
Relying on a single vendor or a homogeneous cybersecurity infrastructure creates a single point of failure. When an organization’s entire security infrastructure hinges on one provider, any failure—whether due to a technical glitch, a cyberattack, or a natural disaster—can have catastrophic consequences. The CrowdStrike incident is a prime example: organizations that depended solely on CrowdStrike for endpoint protection were left scrambling when the system failed.
Moreover, a uniform cybersecurity approach makes it easier for cybercriminals to design attacks that can penetrate defenses. If every layer of security is built using similar or the same tools, once a vulnerability is found, it can be exploited across the entire system. Diversifying the tools and vendors in your cybersecurity infrastructure can create a more complex and resilient defense, where the failure of one component does not necessarily lead to a total breakdown.
The CrowdStrike outage in July 2024 resulted in substantial financial damages, with widespread disruptions across multiple industries. The faulty update, which affected approximately 8.5 million Windows devices, led to a cascade of system crashes and service failures.
The overall economic impact is estimated to be over $5.4 billion in losses, with the hardest-hit sectors being healthcare, banking, and transportation:
- Healthcare: The sector faced around $1.94 billion in losses, mainly due to delays and cancellations in medical services and difficulties in managing emergency responses.
- Banking: Financial institutions encountered about $1.15 billion in damages, with disruptions in online banking, ATMs, and other critical operations.
- Airlines: The aviation industry, including major airlines like Delta and American Airlines, experienced around $860 million in losses. Delta alone reported a $550 million impact, which included flight cancellations and operational disruptions.
These figures reflect both direct revenue losses and the broader economic impact due to the outage, with only a small percentage likely covered by cybersecurity insurance policies.
Strategies for Diversifying Digital and Cybersecurity Infrastructure

- Multi-Vendor Strategy: Engaging multiple cybersecurity vendors can help mitigate risks. By distributing critical functions across different providers, organizations can ensure that a failure in one system does not completely incapacitate their security defenses. For instance, employing one vendor for endpoint protection, another for threat intelligence, and a third for network security can create a layered security approach.
- Hybrid Cloud Solutions: As more organizations move to the cloud, relying on a single cloud service provider can be risky. A hybrid cloud strategy, which uses a mix of on-premises, private, and public cloud services, can offer greater flexibility and security. In case one service provider experiences an outage, the others can continue to operate, ensuring business continuity.
- Regular Security Audits and Updates: Continuous monitoring, regular audits, and timely updates are crucial to maintaining a robust cybersecurity posture. Organizations should not only rely on their vendors to provide security updates but also perform independent audits to identify potential weaknesses that may have been overlooked.
- Backup and Redundancy Planning: Having a comprehensive backup and redundancy plan is essential. This includes not only backing up data but also having redundant systems that can take over in the event of a primary system failure. Regular testing of these backups and redundancies ensures they will work when needed.
- Training and Awareness: Human error remains a significant factor in cybersecurity breaches. Regular training and awareness programs can help employees recognize and avoid potential threats. Moreover, a well-informed team can quickly adapt to using alternative tools or systems in the event of a failure in the primary cybersecurity infrastructure.
Building Resilience Through Diversity

The CrowdStrike outage serves as a cautionary tale for organizations relying too heavily on a single cybersecurity solution. In an increasingly interconnected digital world, diversification is not just a strategy—it is a necessity. By adopting a diversified digital and cybersecurity infrastructure, organizations can build resilience against disruptions, reduce the risk of cyberattacks, and ensure the continuity of their operations in the face of unforeseen challenges.
Organizations must take proactive steps to analyze their current cybersecurity strategies, identify potential vulnerabilities, and implement diverse solutions that will protect them not only from the known threats of today but also from the unknown risks of tomorrow. The future of digital security depends on our ability to anticipate and mitigate the ever-evolving landscape of cyber threats, and diversification is key to staying ahead.